a·gen·tic a·gil·i·ty
Removing ACL's for dead AD accounts
TL;DR; Explains how to identify and remove access control entries (ACLs) for deleted Active Directory accounts using .NET, including challenges and code examples for automation.


TL;DR; Explains how to identify and remove access control entries (ACLs) for deleted Active Directory accounts using .NET, including challenges and code examples for automation.


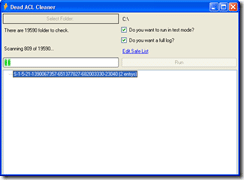 I have run into a very vexing problem with one of my applications. I was asked to provide an application that would fin all of the permissions set against Active Directory accounts that have been since removed. These normally show up in the permissions dialogs for folders as the full SID of the account as there is no longer nay way to look it up in Active Directory.
I have run into a very vexing problem with one of my applications. I was asked to provide an application that would fin all of the permissions set against Active Directory accounts that have been since removed. These normally show up in the permissions dialogs for folders as the full SID of the account as there is no longer nay way to look it up in Active Directory.
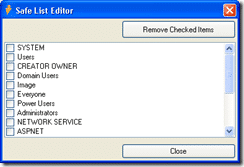 I have written a nice little threaded application that lets you select a folder and it finds all of the dead accounts. What it actually does is verify all accounts against Active Directory and flags them if they are not found. This will have the side effect of finding groups and local accounts and thinking they are dead as well. To solve this problem I added a “Safe List” of accounts and as way to add them from the GUI. The system then ignores any account names that are in this list.
I have written a nice little threaded application that lets you select a folder and it finds all of the dead accounts. What it actually does is verify all accounts against Active Directory and flags them if they are not found. This will have the side effect of finding groups and local accounts and thinking they are dead as well. To solve this problem I added a “Safe List” of accounts and as way to add them from the GUI. The system then ignores any account names that are in this list.
All is well…
But not really. As I moved on to actually deleting the offending ACL’s on request, I found it was a little more difficult to actually delete them as .NET seams to ignore my code…
1Private Sub RemoveACL(ByVal DirectoryName As String, _ 2 ByVal IdentityReference As Security.Principal.IdentityReference) 3 Dim DS As DirectorySecurity 4 DS = System.IO.Directory.GetAccessControl(DirectoryName) 5 6 DS.PurgeAccessRules(IdentityReference) 7 DS.PurgeAuditRules(IdentityReference) 8 9 System.IO.Directory.SetAccessControl(DirectoryName, DS) 10End Sub
Now, this code is fairly simple. First we get the directory security object, then we change the directory security object, and then we save the directory security object.
The “DirectoryName” object contains a CuteFTP folder:
The “IdentityReference” object contains the offending SID:
This code should work, and I have used a similar piece to add permissions, so why on earth can’t I remove them!
UPDATE: I have added a question about this to the MSDN Forums
Technorati Tags: .NET
If you've made it this far, it's worth connecting with our principal consultant and coach, Martin Hinshelwood, for a 30-minute 'ask me anything' call.
We partner with businesses across diverse industries, including finance, insurance, healthcare, pharmaceuticals, technology, engineering, transportation, hospitality, entertainment, legal, government, and military sectors.

Healthgrades

Deliotte

Bistech

Lean SA

ProgramUtvikling

Freadom

Teleplan

Epic Games

SuperControl

Lockheed Martin

Ericson

Kongsberg Maritime

Xceptor - Process and Data Automation

Emerson Process Management

Flowmaster (a Mentor Graphics Company)

Alignment Healthcare

Sage

Capita Secure Information Solutions Ltd

Department of Work and Pensions (UK)

Nottingham County Council

Washington Department of Transport

New Hampshire Supreme Court

Washington Department of Enterprise Services

Ghana Police Service

MacDonald Humfrey (Automation) Ltd.

Alignment Healthcare

Emerson Process Management
NIT A/S

Sage
CR2